双 11 淘宝不打折,云服务器打折,果断买了一个来学习下如何搭建一个可以进行科学上网的梯子.
1.购买域名以及获取证书
因为 Trojan 工作原理是伪装成 HTTPS 流量来躲避 GFW 的检测. 所以我们需要一个域名来获取证书.关于如何购买域名以及获取证书可以参考从0到1构建自己具有https协议的服务器这一篇文章.
不过不同的地方在于安装证书的时候只需要输入
acme.sh --install-cert -d <你购买的域名> --key-file /etc/nginx/ssl/<private key filename>.key --fullchain-file /etc/nginx/ssl/<crt filename>.crt
然后配置 acme.sh 自动更新和自动更新证书
acme.sh --upgrade --auto-upgrade
2.配置 Trojan
1. 首先需要下载 Trojan, 下载地址
2. 配置服务端 Trojan 配置 <private key file path> 和 <cert file path> acme.sh 安装证书命令生成的两个文件路径.最后需要修改的是密码 <password>.
trojan/config.json 文件配置
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
{
"run_type": "server",
"local_addr": "0.0.0.0",
"local_port": 443,
"remote_addr": "127.0.0.1",
"remote_port": 80,
"password": [
"<password>"
],
"log_level": 1,
"ssl": {
"cert": "<cert file path>",
"key": "<private key file path>",
"key_password": "",
"cipher": "ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384",
"cipher_tls13": "TLS_AES_128_GCM_SHA256:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_256_GCM_SHA384",
"prefer_server_cipher": true,
"alpn": [
"http/1.1"
],
"alpn_port_override": {
"h2": 81
},
"reuse_session": true,
"session_ticket": false,
"session_timeout": 600,
"plain_http_response": "",
"curves": "",
"dhparam": ""
},
"tcp": {
"prefer_ipv4": false,
"no_delay": true,
"keep_alive": true,
"reuse_port": false,
"fast_open": false,
"fast_open_qlen": 20
},
"mysql": {
"enabled": false,
"server_addr": "127.0.0.1",
"server_port": 3306,
"database": "trojan",
"username": "trojan",
"password": "",
"key": "",
"cert": "",
"ca": ""
}
}
3. 添加一个 启动 Trojan 的配置文件 sudo vim /etc/systemd/system/trojan.service
trojan.service 配置文件
1
2
3
4
5
6
7
8
9
10
11
12
13
14
[Unit]
Description=trojan
After=network.target
[Service]
Type=simple
PIDFile=/usr/src/trojan/trojan.pid
ExecStart=/usr/src/trojan/trojan -c /usr/src/trojan/config.json -l /usr/src/trojan/trojan.log
ExecReload=/bin/kill -HUP \$MAINPID
Restart=always
RestartSec=1s
[Install]
WantedBy=multi-user.target
4. sudo systemctl restart trojan启动 Trojan, sudo systemctl enable trojan 设置 Trojan 开机自启,最后 systemctl status trojan -l 查看下 Trojan 服务目前状态.
5. 因为申请的证书只有3个月有效期,所以每3个月都需要重启下 Trojan,不过我们可以使用 crontab 来定时任务来解决这个问题.sudo -u <username> crontab -e 添加一条定时任务 0 0 1 * * killall -s SIGUSR1 trojan.
3.配置 nginx 来防止恶意探测
1. 安装 nginx sudo apt update && sudo apt install -y nginx
2. 这次我们并不需要修改 nginx的 /etc/nginx/nginx.conf 配置文件.首先我们执行 sudo rm -f /etc/nginx/sites-enabled/default && sudo rm -f /etc/nginx/sites-available/default
3. 执行 sudo vim /etc/nginx/sites-available/<your domain> 然后添加如下配置, <your domain> 替换成你购买的域名, <any activity domain> 随便写一个没有敏感信息的网站, <yoru server ip 填入你服务器的 ip 地址.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
server {
listen 127.0.0.1:80 default_server;
server_name <your domain>;
location / {
proxy_pass <any activity domain>;
}
}
server {
listen 127.0.0.1:80;
server_name <yoru server ip>;
return 301 https://<your domain>$request_uri;
}
server {
listen 0.0.0.0:80;
listen [::]:80;
server_name _;
location / {
return 301 https://$host$request_uri;
}
}
4. sudo systemctl restart nginx && sudo systemctl enable nginx && sudo systemctl status nginx 重新启动下 nginx.
5. 测试下访问我们的服务器. 1.直接在浏览器输入 ip ; 2.https://{ip}; 3.{your domain} 这三种情况配置正确的情况都会被重定向到配置的 <any activity domain>
4. Trojan 客户端配置
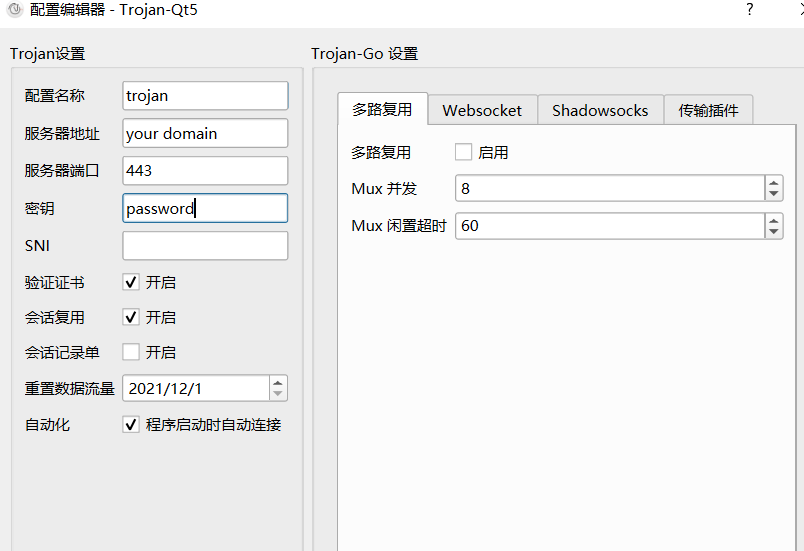
1. 我使用过的 Trojan 图形化客户端是这个 trojan-qt, 下载地址, 图上的配置只需要填入 服务器地址,端口号(默认443), 密钥(就是配置的 password)
2. 目前的话我并没有使用图形化界面的客户端, 这里附上我的配置文件,只需要修改两个配置 <your domain> 和 <password>, 这个方式配置 Trojan 开机自启参考使用frp实现windows远程桌面连接这篇文章的类似操作.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
{
"run_type": "client",
"local_addr": "127.0.0.1",
"local_port": 51837,
"remote_addr": "<your domain>",
"remote_port": 443,
"password": [
"<password>"
],
"log_level": 1,
"ssl": {
"cert": "",
"cipher": "ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384",
"cipher_tls13": "TLS_AES_128_GCM_SHA256:TLS_CHACHA20_POLY1305_SHA256:TLS_AES_256_GCM_SHA384",
"prefer_server_cipher": true,
"alpn": [
"http/1.1"
],
"alpn_port_override": {
"h2": 81
},
"reuse_session": true,
"session_ticket": false,
"session_timeout": 600,
"sni": "",
"verify": true,
"verify_hostname": true,
"plain_http_response": "",
"curves": "",
"dhparam": ""
},
"tcp": {
"prefer_ipv4": false,
"no_delay": true,
"keep_alive": true,
"reuse_port": false,
"fast_open": false,
"fast_open_qlen": 20
},
"mysql": {
"enabled": false,
"server_addr": "127.0.0.1",
"server_port": 3306,
"database": "trojan",
"username": "trojan",
"password": "",
"cafile": ""
}
}